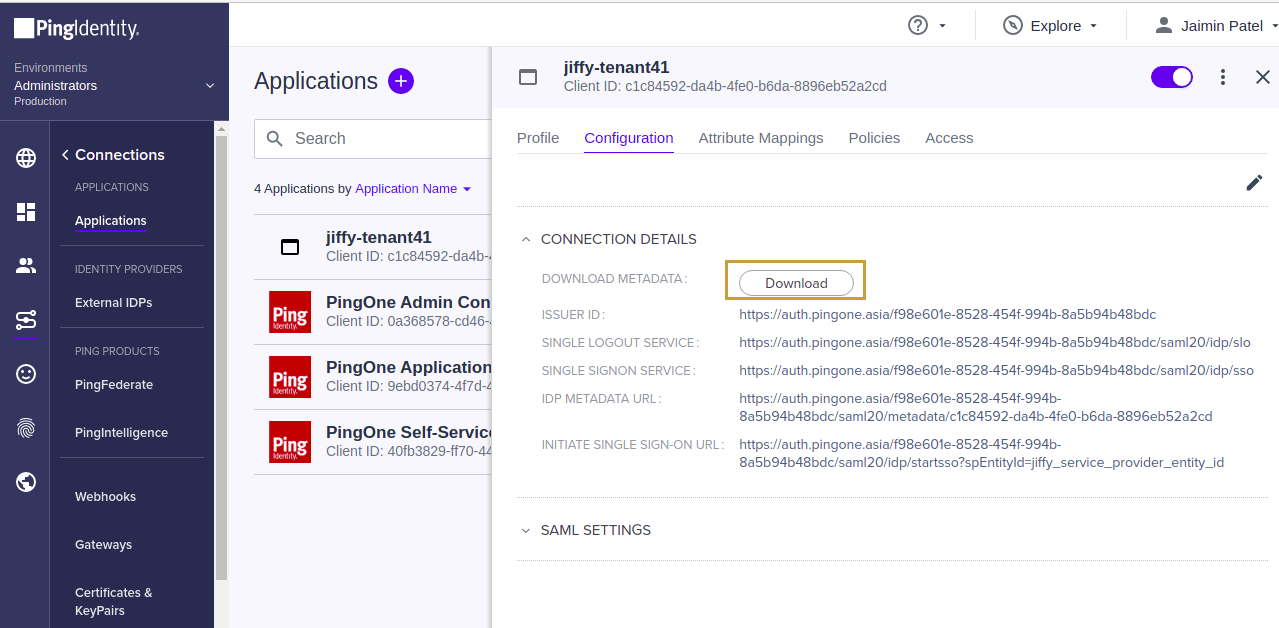
Generate IdP Metadata File
Last Updated: Mar 8, 2023

Last Updated: Mar 8, 2023
These are public APIs and no authentication is required.
The first two steps are to be completed from the Jiffy end.

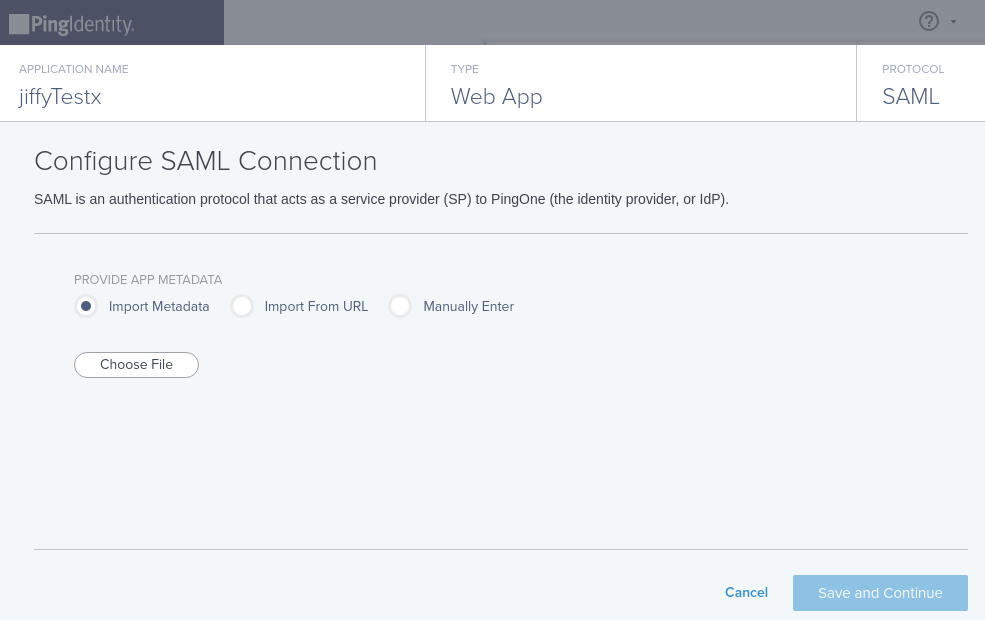
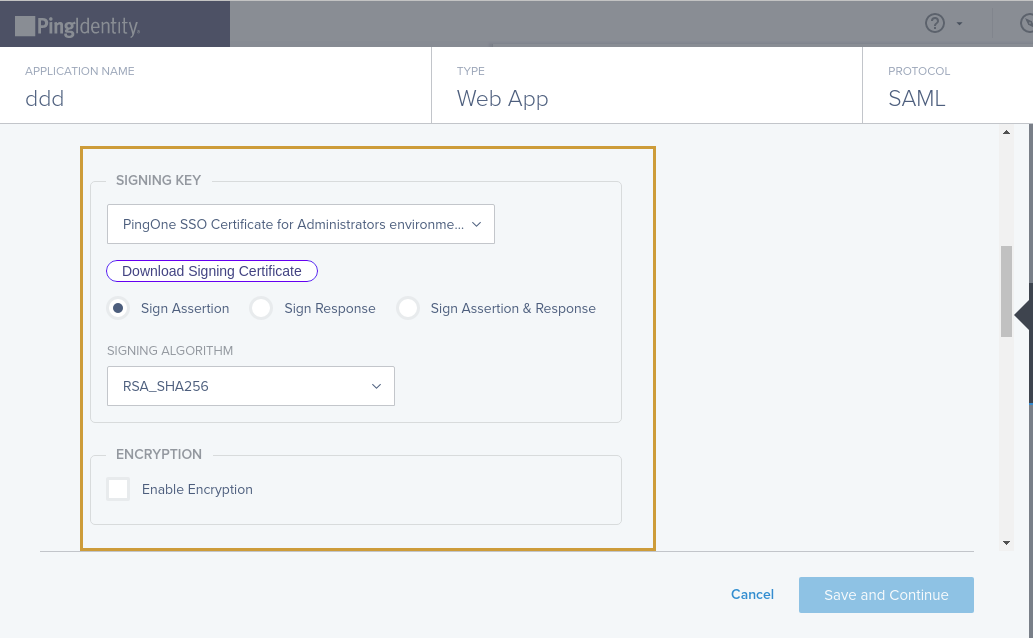
Jiffy supports all three signing options. On Jiffy side,
- If it detects Signed Signature in Response, then the same is validated.
If it detects Signed Signature in Assertion, then the same is validated. If it detects Signed Signature in both Response and Assertion, it validates both.
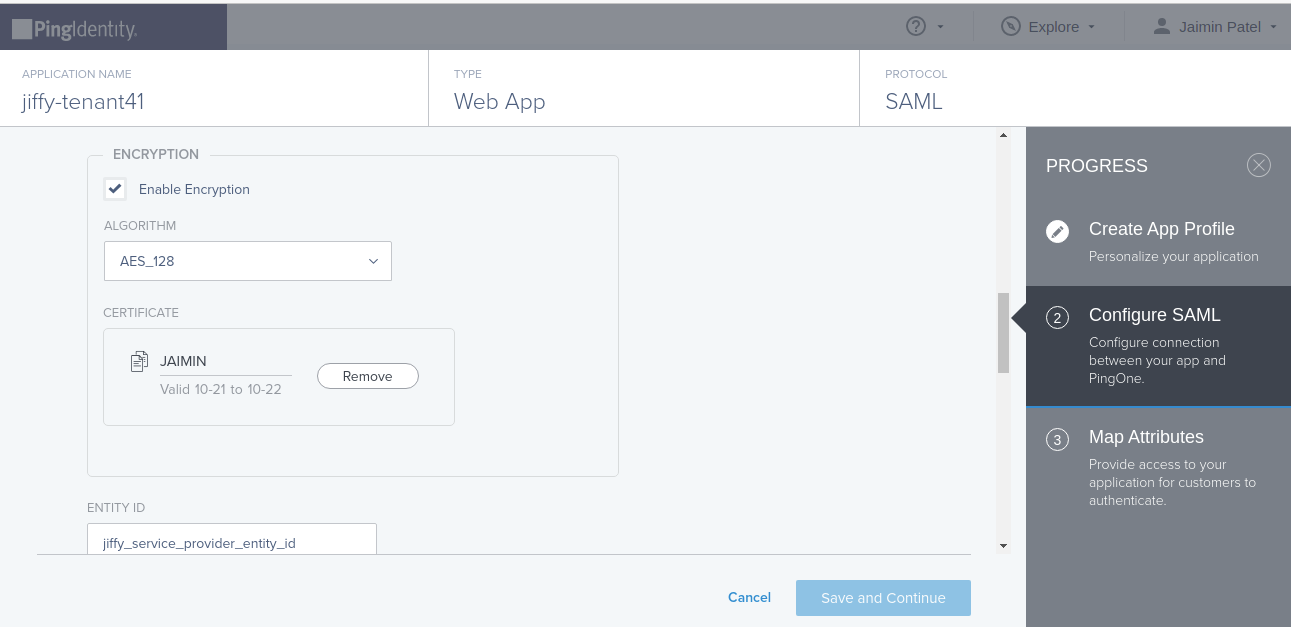
Jiffy supports decryption of Assertion that is encrypted using a public certificate only, downloaded using the endpoint API that Jiffy has exposed.

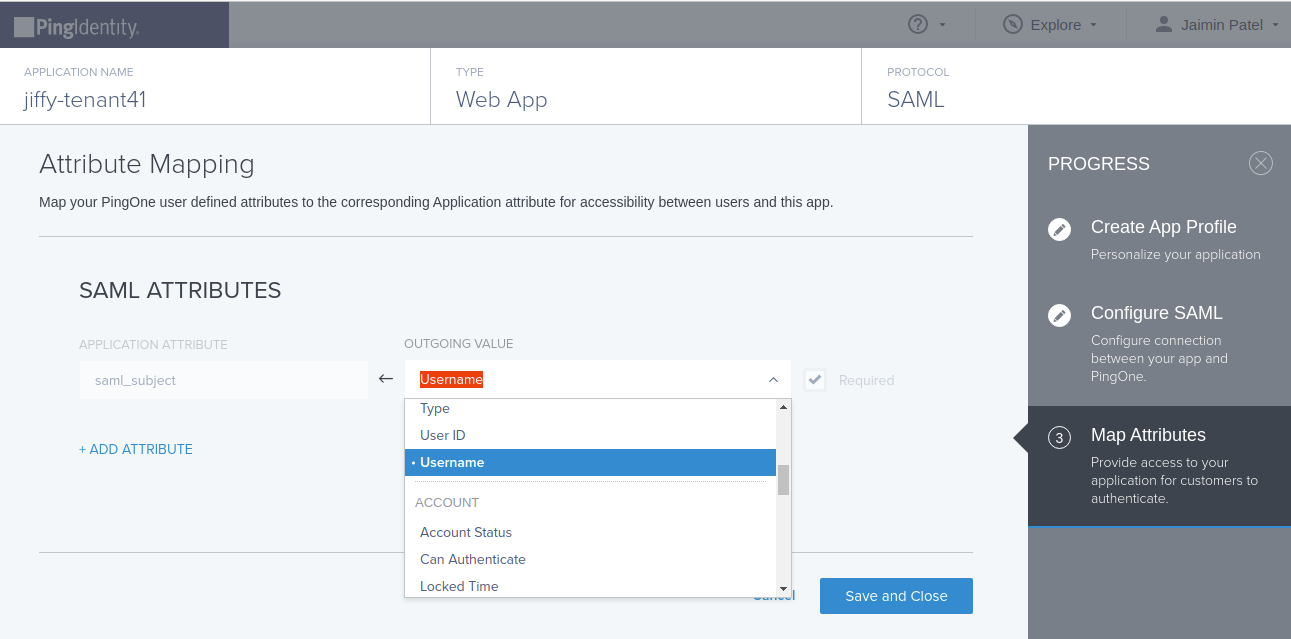
Jiffy identifies username as a unique identifier in the SAML Assertion.
 You will be redirected to applications listing page.
You will be redirected to applications listing page.